New Packet Power products deliver cost-effective, time-saving BCMS solutions
Packet Power is excited to add two models to our set of branch circuit monitoring retrofit solutions and an industry-leading way to share monitoring...
3 min read
![]() Paul Bieganski
:
Dec 12, 2017 9:00:00 AM
Paul Bieganski
:
Dec 12, 2017 9:00:00 AM
Security and safety are the foremost concerns of anybody deploying and managing an energy and environmental monitoring solution within a data center or any other networked environment such as a building or factory floor. The system being monitored and the systems performing the monitoring deploy exceedingly complex technologies. Unfortunately, complexity tends to lead to side effects and unintended consequences.
We have all heard of the original Internet worm, Stuxnet, ransomware and dozens of other public and not so public incidents involving accidental or malicious disruptions spread and delivered through computer networks. At times, the complexity of the problem seems very daunting, despite the acronym soup of safe-sounding certifications and assurances from vendors. Luckily, there are some basic rules that ANY technology has to obey.
Welcome to the laws of physics. Science fiction notwithstanding, all technologies available today (still) have to obey them. It turns out that the same laws can be used as common sense when securing monitoring solutions.
If your task is to prevent your favorite bowling ball (feel free to insert your favorite piece of sports equipment in this explanation) from hitting you on the head in the middle of the night, which solution should you choose?
The answer is of course B. Notice that B also has the added benefit of being provably safe. Unless gravity suddenly reverses itself, the ball is not going to rise from the floor. It is impossible for it to hit you. Physics works!
With solution A, the burden of proof is on the barriers holding the ball and the alarm system. Will it work? If it fails, you will get hit on the head! With solution B, you don't have to worry. There is nothing to fail, so you can sleep well.
This is a simplistic example, but it is eerily close to what happens in monitoring systems safety and security. It turns out that in monitoring systems, it is also possible to choose solutions that make many security threats simply impossible or very unlikely to occur, thus allowing you to sleep better.
Let's review four basic features that can make your monitoring system provably more secure.
Access control: Keep networks separate
Monitoring networks should not have access to critical business data networks. This usually takes the form of firewalls, virtual networks and advanced authentication. A simpler, physically secure solution is a true, physical network separation. If the monitoring system is truly out-of-band (i.e. does not use the same network as business data and is physically isolated from it), it cannot be used to breach business data. Even if the monitoring network is completely compromised, the business data will remain secure.
Information security: Keep data separate
Business data should not "leak" through monitoring networks. The simple solution is strangely similar to the bowling ball solution: Do not put any business or even business-adjacent data on the monitoring network. Monitoring networks should only carry raw physical measurements and identifiers. They should not carry any data that would allow anybody to match it to business data. In most cases, the monitoring network doesn't need to know much to do its job. Whatever security measures are in place, you should assume that they might get compromised. If the data isn't critical to begin with, its exposure will not be critical either.
Reliability: Don't switch it
Monitoring systems should never disrupt the power they monitor. "Can somebody use the monitoring system to shut off my power?" is one of the most common questions we get. It turns out that most remote power switching solutions are never used, which means they should be eliminated. The simplest (and only provably correct!) solution is to remove switching capability altogether. A system without a remote switch cannot be remotely turned off.
Data visibility: Make it truly one-way
A network device using a physically one-way optical fiber such as Packet Power's Data Diode resembles a one-way mirror for data. This device can provide a secure transfer of select data from one network to another without exposing the source network in any way. A Data Diode solution allows monitoring data collected on a completely isolated network to be securely and reliably exposed to another network without creating any physical or information risk to the source network.
Keep your networks separate, keep your data separate, avoid monitoring systems with power switching capability and make your data tranfers truly one-way. These four features can make your monitoring system provably more secure. All of them have been incorporated into Packet Power's monitoring systems.
So put that bowling ball under your bed and sleep well.
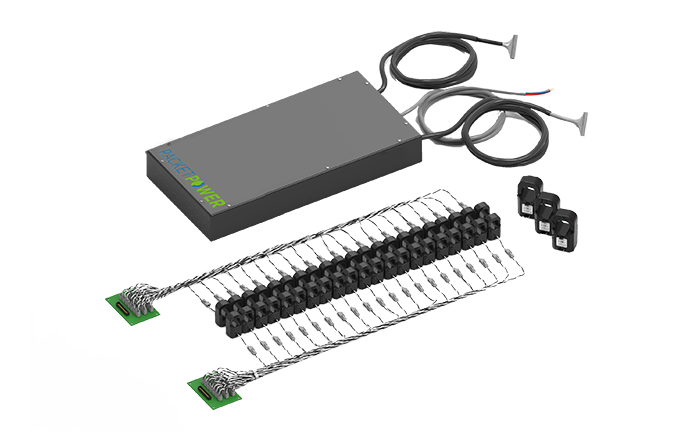
Packet Power is excited to add two models to our set of branch circuit monitoring retrofit solutions and an industry-leading way to share monitoring...

The rise of the "Internet of Things" (IoT) has made it possible to monitor and control an incredibly wide range of devices using wireless...

It has never been more important for your critical infrastructure to be up and running. Remote monitoring helps ensure your facilities are operating...